Executive Summary
Organizations utilizing Microsoft Sentinel for an extended period may have initially configured it without adhering to contemporary best practices. When I first implemented Microsoft Sentinel—then known as Azure Sentinel—limited guidance was available for optimal setup and management. This article outlines best practices for configuring Sentinel in alignment with current standards and provides a structured approach to migrating Sentinel to a new subscription. By following these recommendations, organizations can optimize their security posture, improve efficiency, and streamline long-term management.
Best Practices
Subscription and Resource Organization
When I first deployed Microsoft Sentinel six years ago, Microsoft's security best practices were still evolving. A key improvement in current recommendations is the use of a dedicated subscription for security solutions. This architectural approach enhances security by isolating critical resources from other workloads and simplifies access control. It also reduces the risk of unintended permission escalation and ensures that Sentinel remains insulated from non-security-related configurations.
Every Azure environment includes a default root subscription. While deploying Sentinel within the root subscription may seem convenient, it can lead to long-term complications, particularly in managing roles and permissions. Assigning Sentinel-specific roles and integrating AI-driven security mechanisms can become cumbersome when security tools are not properly segmented. Additionally, having a separate security subscription allows for easier auditing and monitoring, as well as improved cost tracking.
Recommended Configuration:
- Establish a dedicated security subscription separate from the root subscription.
- Create a designated resource group for Microsoft Sentinel, ensuring that the Log Analytics workspace resides within this group.
- Introduce an additional resource group (e.g.,
MS-Sentinel-Resources) for third-party connectors and Azure Monitor Agent (AMA) components deployed via Azure Arc. - Leverage Azure Active Directory (AAD) groups to manage role-based access control (RBAC) instead of assigning permissions to individual users.
- Plan Sentinel role assignments in advance using Microsoft’s RBAC best practices to streamline permission management.
- Document all role assignments and permissions to ensure consistency and ease of auditing.
- Regularly review subscription policies and configurations to align with Microsoft's latest security recommendations.
Log Retention Strategies
Since Sentinel operates atop a Log Analytics workspace, defining a comprehensive log retention policy is essential. By default, logs are retained for 30 days, which may not satisfy regulatory or operational requirements. To optimize retention:
- Extend interactive retention to 90 days for enhanced query capabilities.
- Archive logs older than 90 days to reduce storage costs while maintaining compliance.
- Align retention policies with regulatory mandates to meet compliance obligations and minimize risk exposure.
- Utilize Azure Storage for long-term retention if compliance requires logs to be stored beyond the default retention periods.
- Implement log filtering strategies to avoid excessive ingestion of non-critical data, helping to optimize costs.
- Regularly review and adjust log retention policies to ensure they remain aligned with evolving compliance and business needs.
Migrating Microsoft Sentinel to a New Subscription
Step 1: Evaluate and Optimize Existing Connectors
Before initiating the migration, conduct a thorough assessment of active connectors in your Sentinel deployment. Microsoft has deprecated several connectors over time, making this an opportune moment to remove outdated configurations. This process helps eliminate redundant data ingestion, reduces costs, and improves overall efficiency.
- Identify mission-critical connectors and prioritize their migration.
- Decommission obsolete or redundant connectors to improve system efficiency.
- Reassess threat intelligence integrations—for instance, Microsoft’s E5 security license includes a built-in threat intelligence feed, potentially replacing third-party integrations.
- Document all connectors and dependencies before migration to prevent disruptions.
- Test new connectors in a controlled environment before implementing them in production.
Step 2: Provision the New Sentinel Environment
Log Analytics workspace data cannot be transferred between workspaces, necessitating a fresh deployment. The migration process involves:
- Deploying a new Log Analytics workspace within the new subscription.
- Configuring security settings and RBAC roles before enabling Microsoft Sentinel.
- Activating Microsoft Sentinel within the newly created workspace.
- Establishing data access policies to maintain security controls.
- Ensuring Azure Monitor integration for improved visibility and performance monitoring.
Step 3: Reestablish and Configure Connectors
Once the new Sentinel instance is operational:
- Deploy the required connectors but postpone data migration until they are properly configured.
- Relocate third-party connectors to the MS-Sentinel-Resources resource group to facilitate better management.
- If using Azure Arc, transition connected resources to the new workspace and update Data Collection Rules (DCRs) accordingly.
- Perform a test ingestion to verify that logs are properly flowing into the new Sentinel instance.
Step 4: Export and Import Analytics Rules
To ensure continuity in threat detection, analytics rules must be migrated:
- Navigate to Sentinel Instance > Configuration > Analytics.
- Click the three-dot menu (
...) in the upper-right corner and select Export.
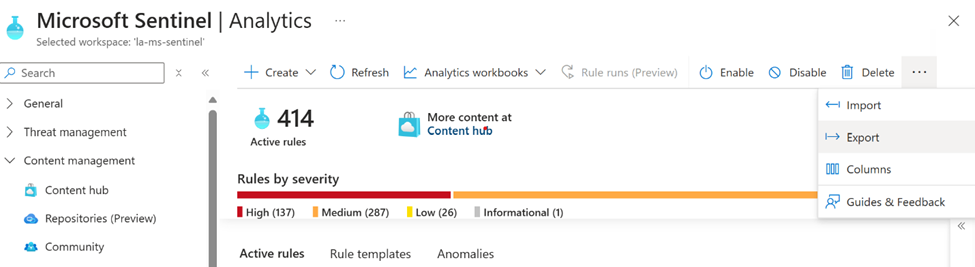
- Save the exported ruleset and import it into the new Sentinel instance.
- Some rules may require generated logs before they can function properly.
- Validate rule dependencies to ensure that required log sources are available.
- Perform a test run to verify that analytics rules are functioning as expected.
Step 5: Deploy ASIM Parsers
Sentinel leverages Advanced Security Information Model (ASIM) parsers for log standardization. Before importing analytics rules, ensure these parsers are activated.
- Access ASIM parsers via: Azure Sentinel Parsers.
- At a minimum, install all ASIM modules to prevent parsing-related errors.
- Regularly update ASIM parsers to ensure compatibility with evolving log sources.
Step 6: Migrate Automation Rules and Logic Apps
Automation rules and Logic Apps must be transitioned carefully:
- Export automation rules via Sentinel > Automation > Export.
- Extract Logic Apps using PowerShell scripts using the script from this stackoverflow Post: Move Sentinel Logic Apps
- After reimporting, reconfigure API connections and update authentication settings.
- Validate automation workflows by running test scenarios.
Step 7: Transition Data Sources
Once the foundational elements are in place, proceed with data migration:
- Minimize transition time to prevent duplicate alerts from two Sentinel instances.
- If integrated with Microsoft Defender XDR, temporarily link both Sentinel environments to streamline the transition.
- Migrate high-priority data sources first to maintain operational integrity.
- Monitor ingestion rates and costs to ensure efficient resource utilization.
Step 8: Final Validation and Optimization
Before decommissioning the previous Sentinel deployment:
- Verify that all critical logs are being ingested into the new Sentinel workspace.
- Validate the effectiveness of analytics rules, alerts, and workbook dashboards.
- Ensure that RBAC assignments are accurately replicated.
- Optimize log filtering configurations to prevent excessive data ingestion costs.
- Conduct performance testing to ensure the new Sentinel instance meets operational requirements.
Conclusion
Migrating Microsoft Sentinel to a new subscription is not inherently complex but requires meticulous planning and execution. Implementing best practices enhances security, streamlines management, and reduces operational overhead.
For those contemplating this transition, my advice is simple—do not delay. The process, while detailed, results in a cleaner, more secure, and more maintainable Sentinel deployment.
If you have insights or experiences with Sentinel migrations, feel free to reach out to me.
