One of my goals is to enable Multi-Factor authentication to access the administrative pages on most systems. The Solarwinds and Microsoft Exchange breach's are two very good examples of why you should enable MFA for administrative interfaces. If your network is compromised and someone obtains your password, they still need a second factor to gain administrative access to key systems. (Including backup systems, but that is another topic for another day)
With that in mind, I set out to enable MFA for both GUI and SSH access when administrating the Citrix ADC. I did not find very good information on how to enable MFA for administrative interfaces. I did read a very vague article on how to use Nfactor to accomplish this, but that only appears to work if you are using token based multi-factor solutions such as RSA. After hours fighting to make it function, I finally have the recipe needed to make this work and I am going to share it here.
Microsoft Azure MFA NPS Extension
The first step is setting up a Microsoft NPS Server that has the Azure MFA NPS extension setup and enabled. I am not going to show you how to configure the NPS extension, but you can find an article on how to configure it here.
Windows Server NPS Configuration
The first step is defining a radius client on your NPS server. Select a name, IP address and a radius shared secret that will be used to authenticate the radius client.
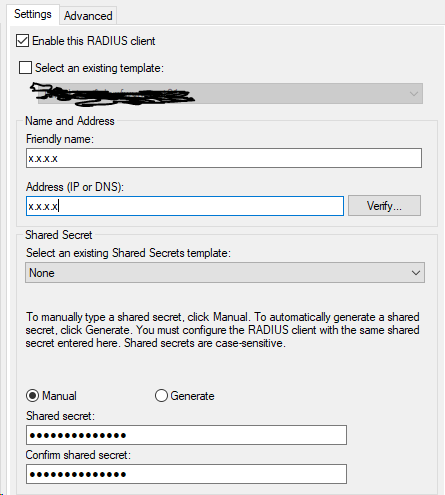
Go to the advanced page and uncheck the Access-Request messages must contain the Message-Authenticator attribute
The next step is to create a connection request policy, make sure it is above the default "Use Windows authentication for all users.
Give the policy a name and then go to conditions.
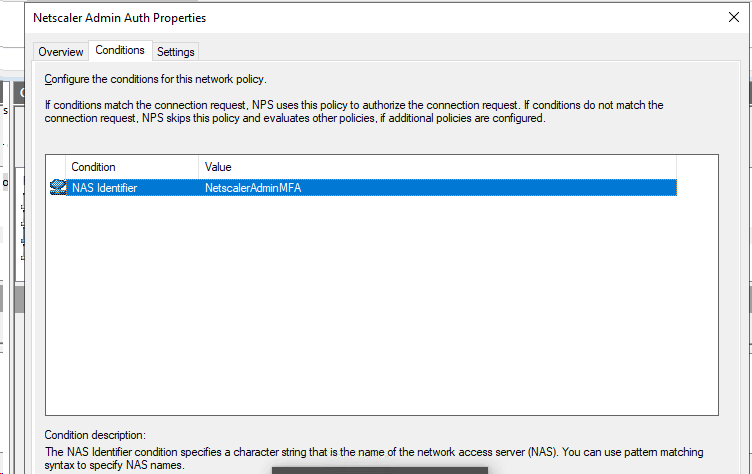
On the conditions page, you will need to create a NAS Identifier, the NAS Identifier is a parameter that the Netscaler ADC will send over to help identify the radius request. It can be named anything you would like, I choose NetscalerAdminMFA for my example.
You then need to go to settings and go to radius attributes and then add a new attribute, select Vendor Specific, select enter vendor code and enter 3845, Select, yes it conforms and select configure attribute.
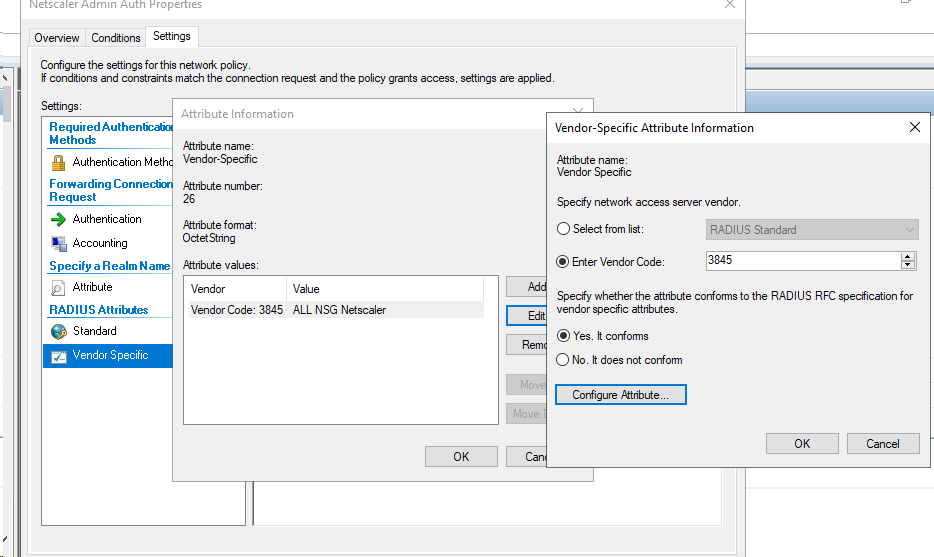
In configure attribute, select 1 for the vendor-assigned attribute number. The attribute value, should be set to the Windows Active Directory Group that the Netscaler has mapped for administrative access and contains the users you have chosen to have administrative rights to the Netscaler. Ih you don't set this field with a group you will not have rights to configure the Netscaler. Select OK and save the policy. This article explains in greater detail how this feature works.
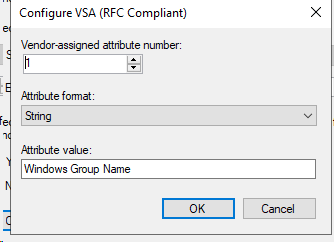
The last step is setting up a network policy. Give the policy a name, select grant access and select ignore user account dial-in properties.
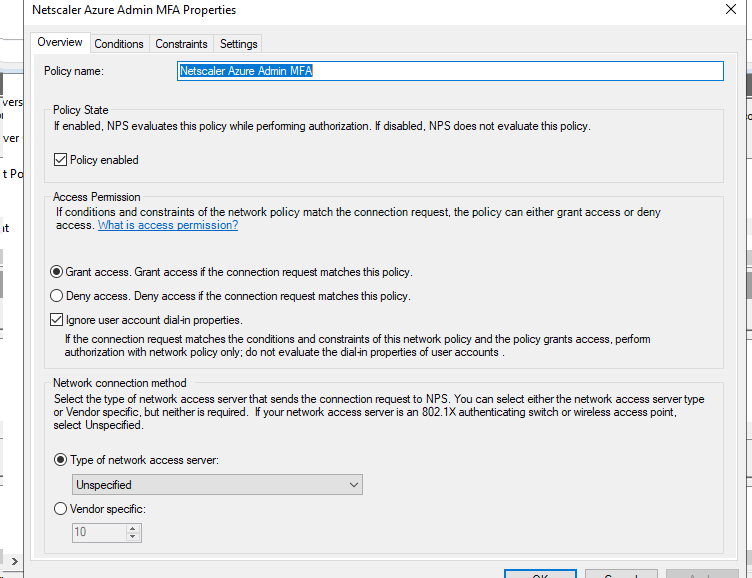
On the conditions page, you will put in the NAS identifier and the Active Directory user group this policy should be applied to. This group should only contain users who you would like to grant administrative access to the Netscaler.
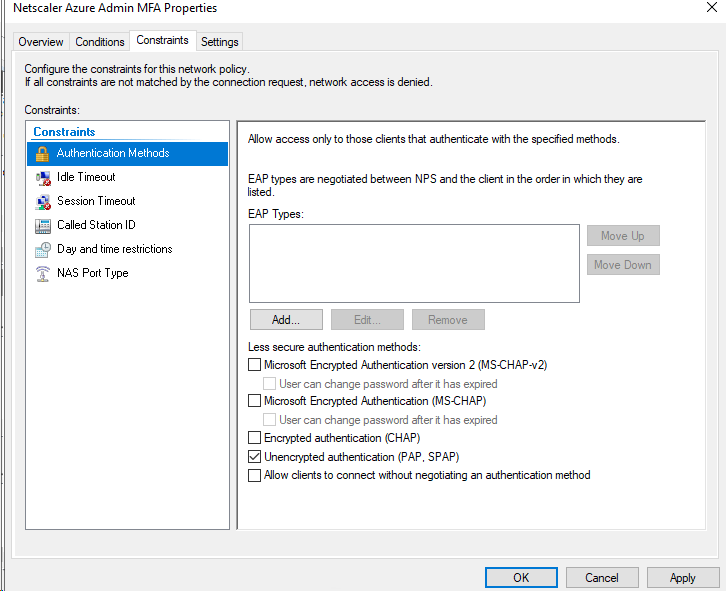
The final setting is on the constraints page, select authentication methods and select unencrypted PAP. This reason to select PAP is it offers the most flexibility with the authentication methods used with Azure MFA.
This information was obtained from this article.
- PAP supports all the authentication methods of Azure AD Multi-Factor Authentication in the cloud: phone call, one-way text message, mobile app notification, OATH hardware tokens, and mobile app verification code.
- CHAPV2 and EAP support phone call and mobile app notification.
Netscaler ADC
On the Netscaler, Go to system, Authentication, Basic Polices, Radius, Servers
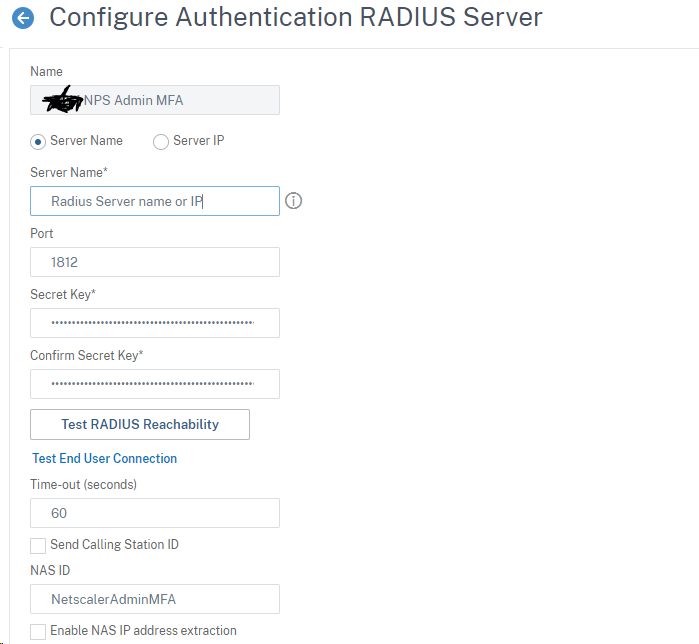
You will add the radius server here. I like to create dedicated radius servers for administrative authentication. The Netscaler allows for multiple radius servers with the same IP address, the NAS identifier is a good way to for the NPS server to identify which policies the radius request should apply to.
Give the radius server a name that will identify the radius server (I like to name it so it clearly states it is for administrative authentication) put the DNS name or IP address in server name and put in your secret key. In the NAS ID field, put the NSA ID you created on your NPS server. This is how the NPS server will be able to identify you are using this radius server for administrative authentication.
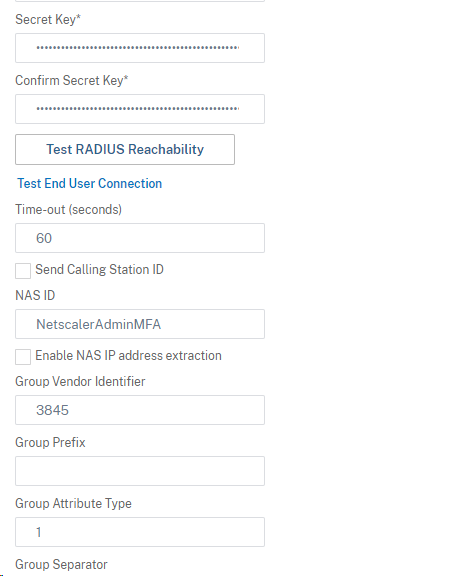
Make sure you put 3845 in the group vendor identifier field and 1 for the group attribute type. If you do not fill those fields in, the Netscaler will ignore the group that is being passed from the radius server. Select ok to save.
Then go to system --> Authentication --> Advanced Policies --> Authentication Policies
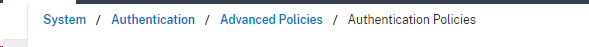
Create a new Authentication Policy. Give it a name, select the action as radius and then set the expression as true and select ok to save.
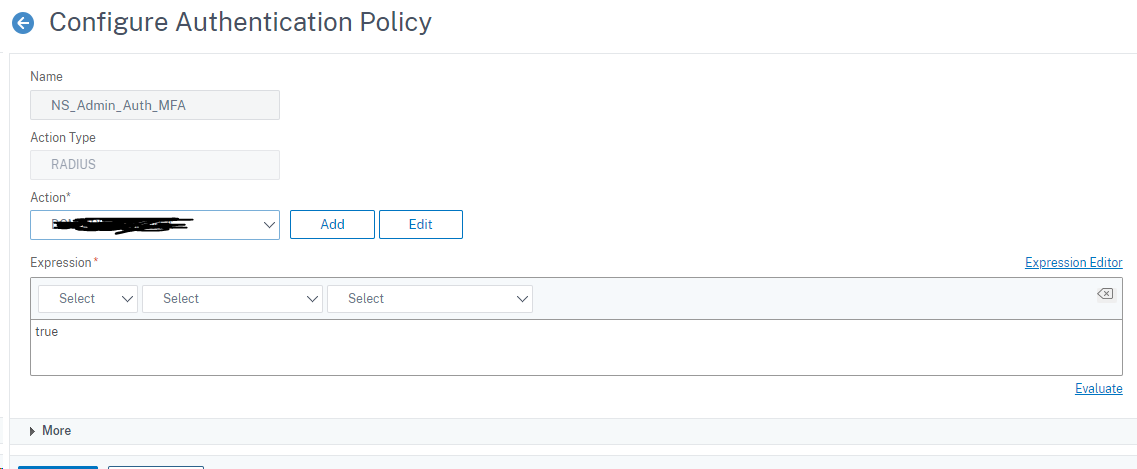
In the same section, go to global binding and bind the policy you just created to global binding as shown below.
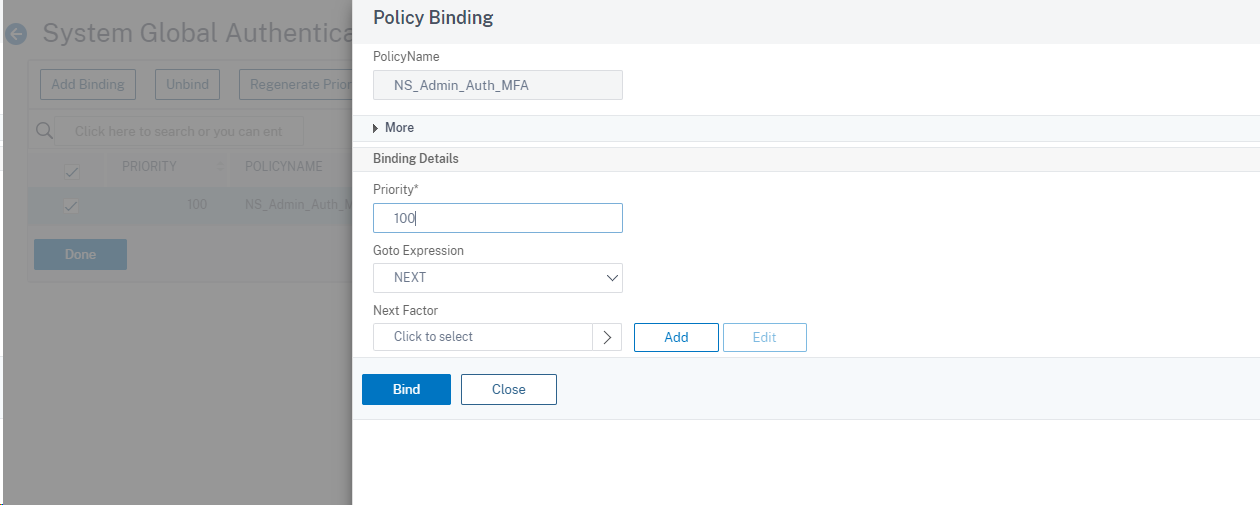
Once this has been completed, you are ready to test. After you put in your user name and password, you should be prompted with a screen that looks like this. Enter your MFA Code and you should be set.
Troubleshooting
If authentication is failing, this is a good article on troubleshooting AAA authentication.
The Microsoft NPS server also has a windows event log that will show you success and failures and will also show you which NPS connection polices you are matching.
Is is also a good idea to make sure that the radius secret is set correctly, the author of this article fought an authentication issue for a few hours only to find out he had not set the radius secret correctly on the Netscaler. Sometimes is is the simple things :)
I hope you find this article useful and helpful
