I thought I would write a quick blog post on something that is easy to implement and will help detect if someone has compromised your network.
The first step is to create a honeypot administrative account in active directory. You create an active directory account. You will want to log on with the account at least once. The reason you need to log on at least once is Active Directory tracks account logons and it is very easy to tell an account has never been used. You want to give this account an enticing name so that if someone does compromise your Active Directory Domain and performs a userdump, it will entice them to use it.
The next step is to set the logon hours so the account never can log in.
The next step is to go to the Azure Sentinel portal, then go to Analytics, then create and select Scheduled query rule.
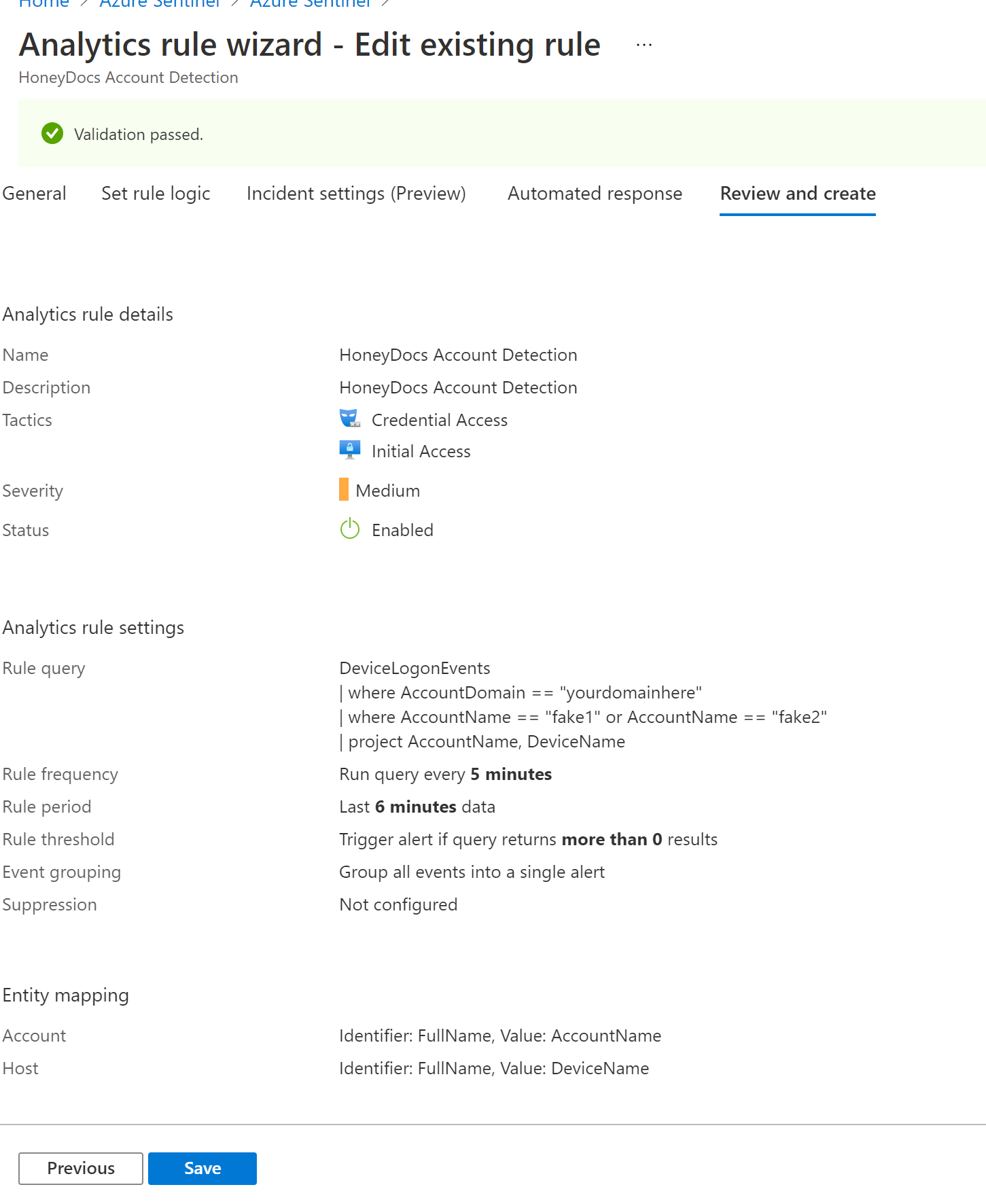
Give the rule a name and description. For tactics, I selected Initial Access and Credential Access, but you can select whatever makes sense in your environment, select next.
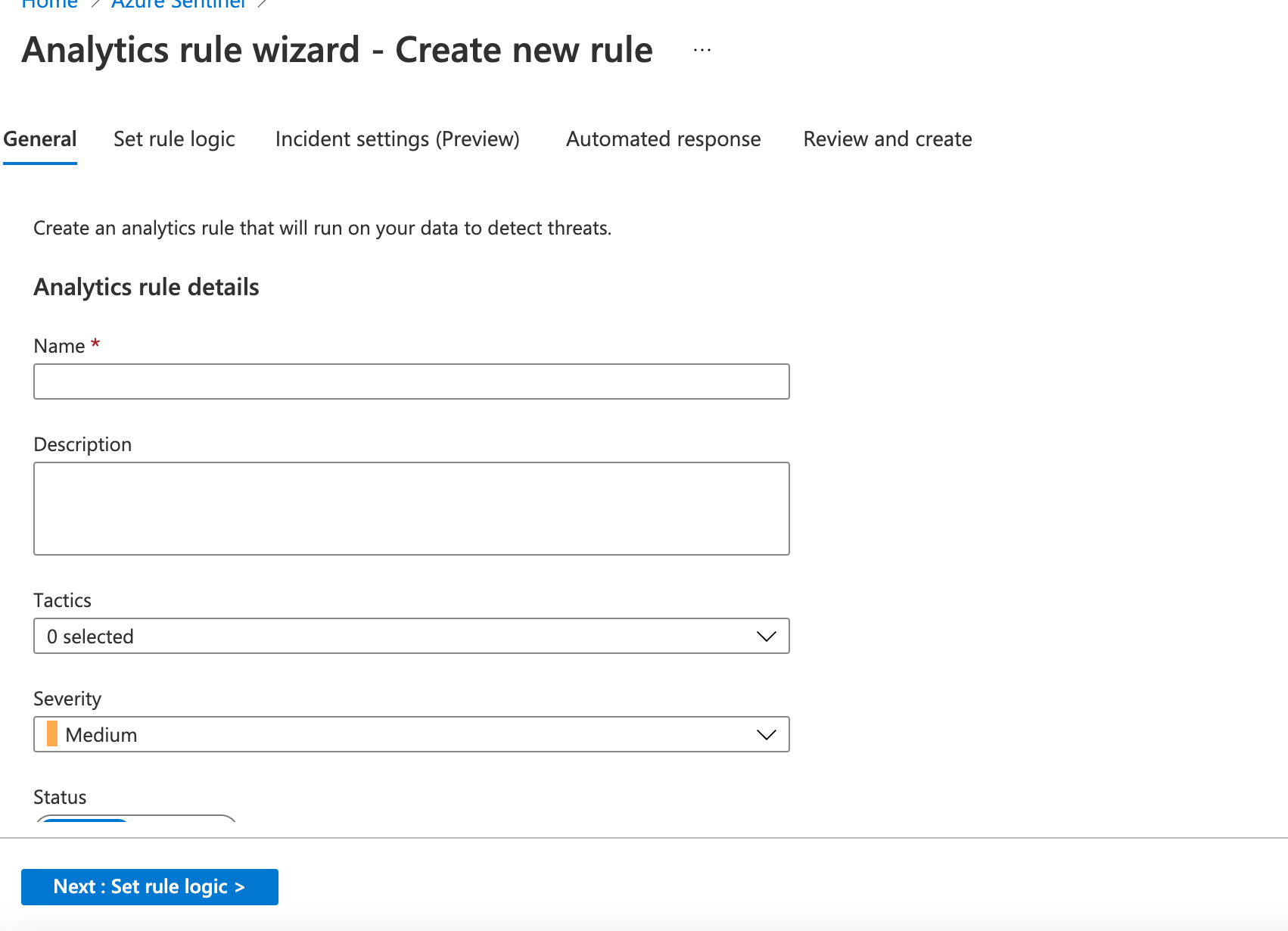
In the Rule query section, you will want to enter the query below. It looks at the device logon events and looks for the honey account. Make sure you update your domain to the domain you are using and update the account name to the account you used as your honey account. (I am also assuming you either have Windows Defender ATP deployed or you have the Azure Sentinel agent deployed and collecting logs on your machines)
DeviceLogonEvents
| where AccountDomain == "yourdomainhere"
| where AccountName == "fake1" or AccountName == "fake2"
| project AccountName, DeviceName
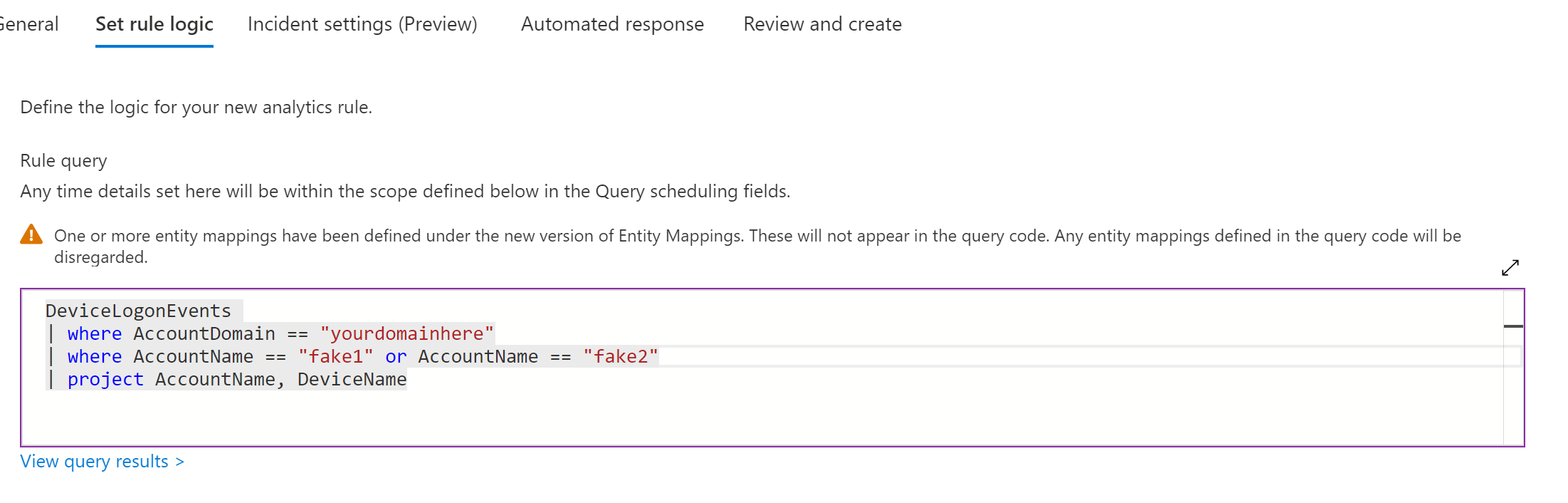
In the Entity mapping configure account and select FullName and Account Name. Select Host and FullName and Devicename. This should put the accountname and the device they attempt access from in the alert
In the Query Schedule, select run query every 5 minutes and lookup data from the last 6 minutes. Also set the alert threshold to great then zero and group events into a single alert.
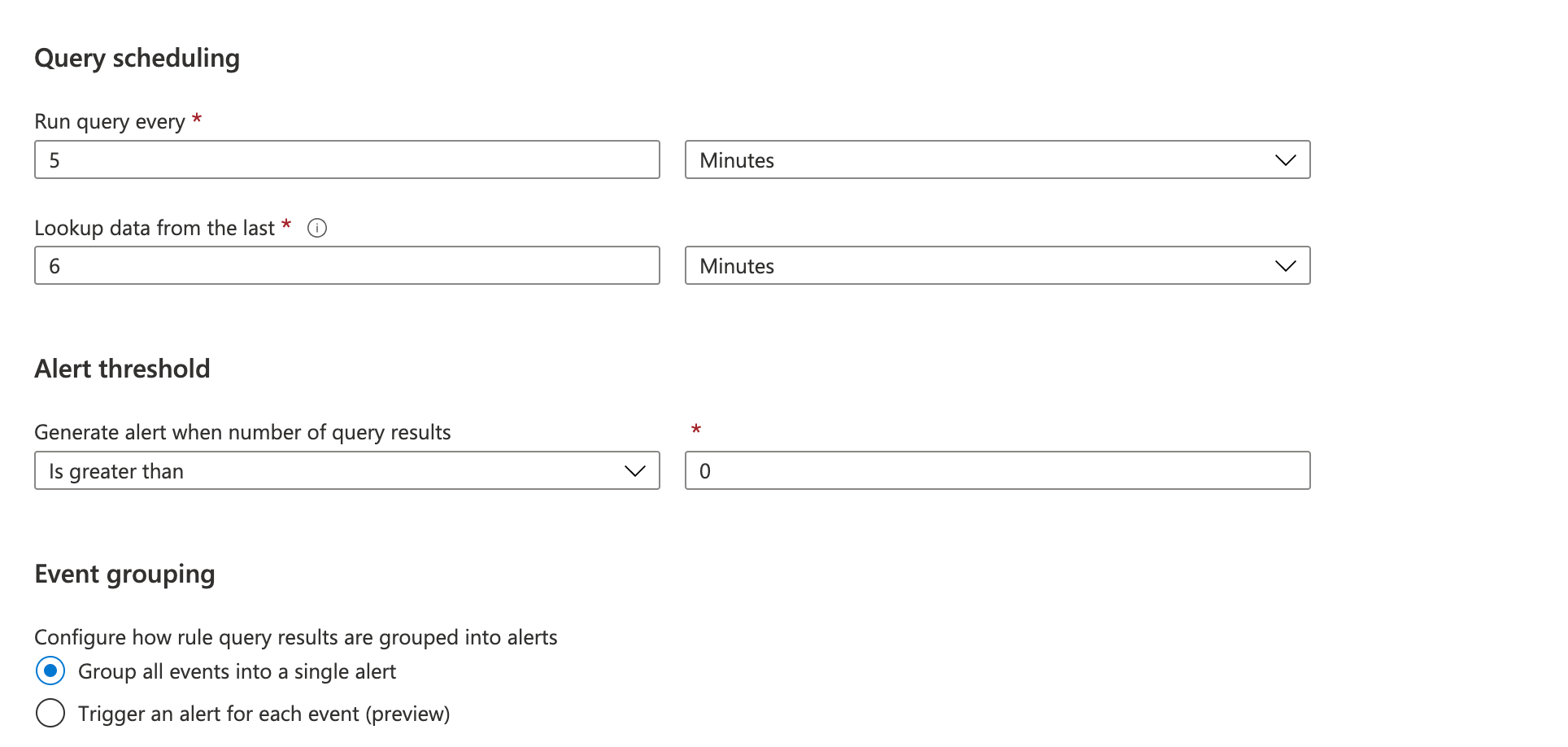
Select Next to go to Incident Settings
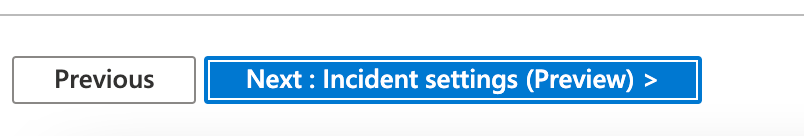
This is a preview feature at the time of this blog post and could change before it goes into full production. Enable the Create incidents from alerts triggered by this analytics rule and select next.
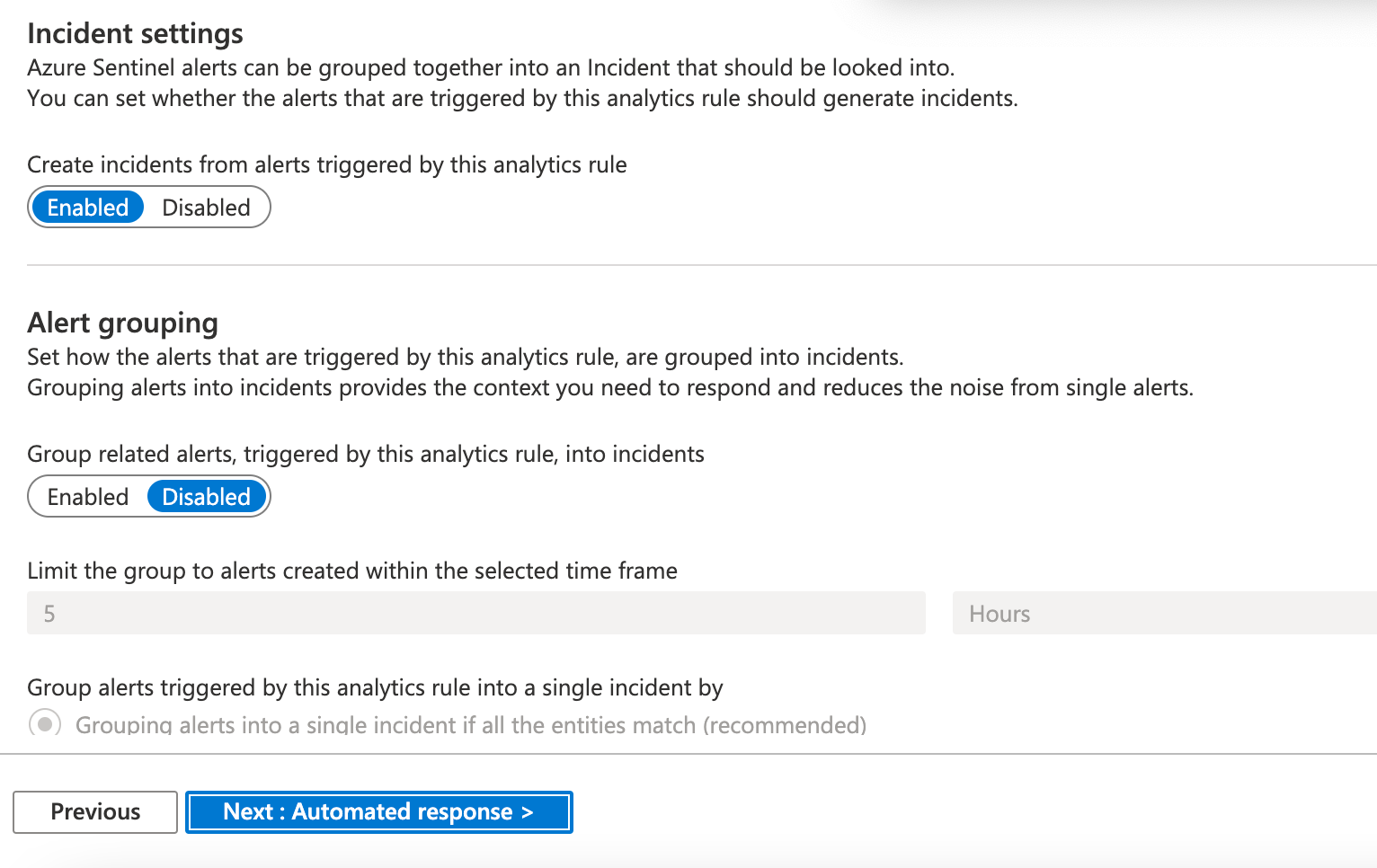
In the Alert automation section, select the alert you would like to use. The alert that I selected is send email notification. I will put a section at the end of this post on how to setup an email notification alert. Make sure it is set to enabled. Select next.
Review the information to make sure it is accurate and select save.
Congratulations, you have a rule that is looking for anyone using the honey account to login to your network.
If you have other accounts you would like to monitor, like a domain admin account that should not be used, you can use the same alert logic to notify you if someone is logging in using an account they should not be using.
I will show you the logic behind the email alert that I used in this example. Go to Azure Sentinel, then automation.
You are creating a logic app, I am not going to show you step by step on how to do that, but I will show you the logic I used to send the alert.
The logic is listed below.
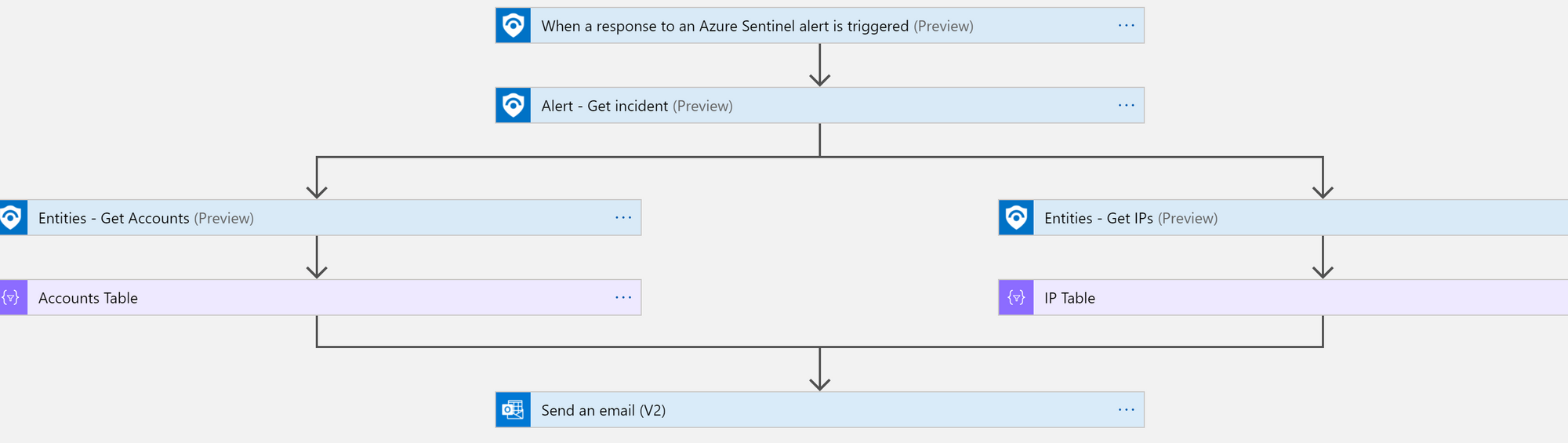
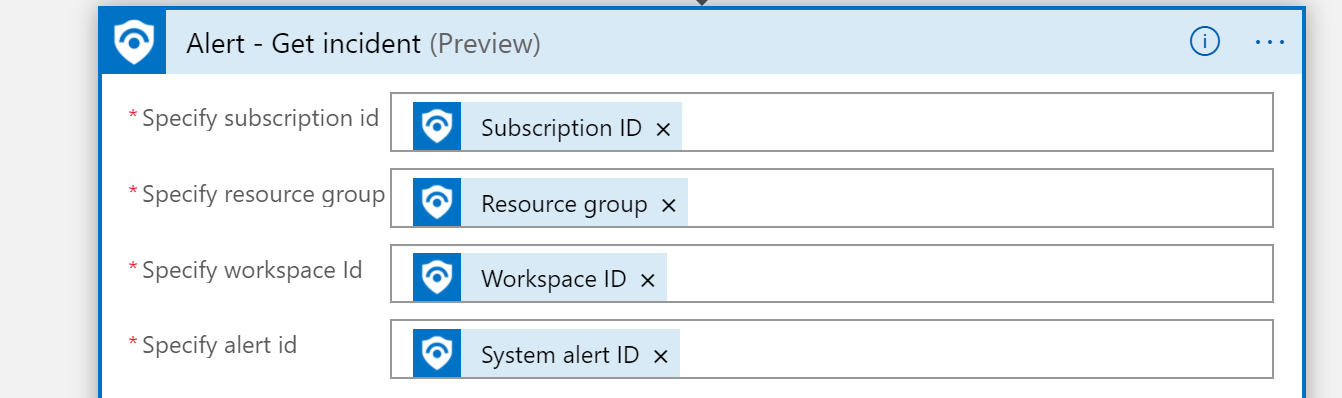
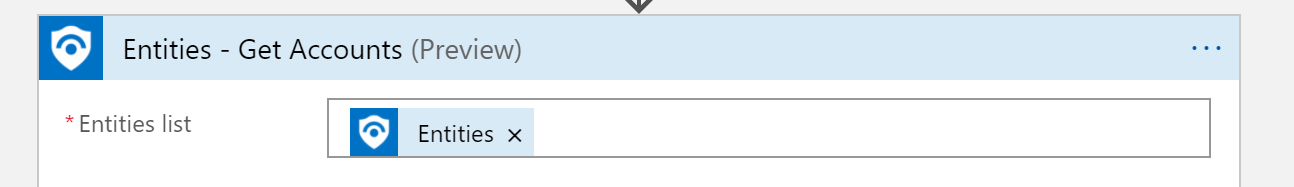
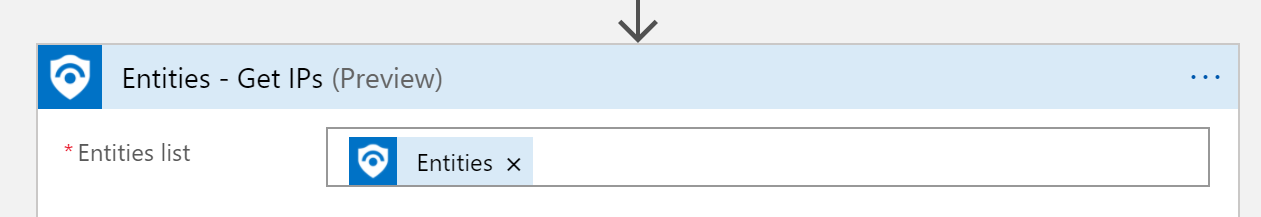
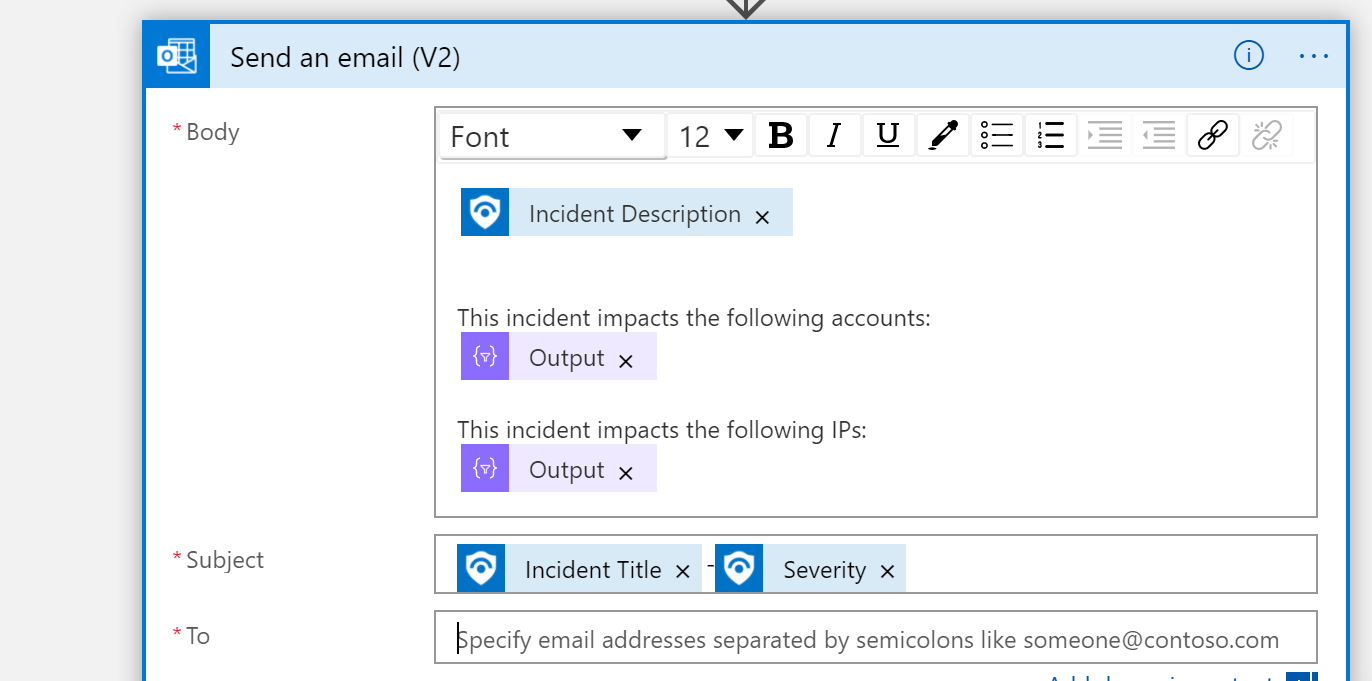
This is another great reference if you want to have all of Sentinel's alerts sent to you via email. Sentinel Email Notification Logic App – Azure Cloud & AI Domain Blog (azurecloudai.blog)
This is a low cost way to setup a trap for attackers who compromise your network and are probing your Active Directory.
I hope you find this useful in your environment.
