If you are like most people I have spoken to, print nightmare adversely affected your end-users and Microsoft did a poor job of rolling out this patch. If you are using Point and Print and anything other than type four print drivers (find out more here about type four print drivers here, you are more than likely using type 3), this patch caused prompting for print drivers if your users were not local administrators on their machines.Which I hope they are not local administrators, that is a very bad practice.
Part of Microsoft's advice it so move to type 4 print drivers, most manufactuers don't have type 4 print drivers available, just type 3. If you are using the HP universal print driver, they only have a type 3 available.
If you are using Point and Print in your environment, you will need to do the following to allow Point and Print to continute to function.
The first thing I would recommend doing is disabling the print spooler on most if not all of your servers. Most servers do not need the print spooler and if the service is disabled you are protected. You will still need to keep it operational on print servers and terminal/citrix servers.
The next step is to follow the guideance in this article, but I will also highlight it step by step. https://support.microsoft.com/en-us/topic/kb5005652-manage-new-point-and-print-default-driver-installation-behavior-cve-2021-34481-873642bf-2634-49c5-a23b-6d8e9a302872
The first item you need too do is add the following to a group policy object that will apply to your computers.
Permit users to only connect to specific print servers that you trust
This policy, Point and Print Restrictions, applies to Point and Print printers using a non-package-aware driver on the server.
Use the following steps:
- Open the Group Policy Management Console (GPMC).
- In the GPMC console tree, go to the domain or organizational unit (OU) that stores the user accounts for which you want to modify printer driver security settings.
- Right-click the appropriate domain or OU and click Create a GPO in this domain, and Link it here.Type a name for the new Group Policy Object (GPO) and then click OK.
- Right-click the GPO that you created and then click Edit.
- In the Group Policy Management Editor window, click Computer Configuration, click Policies, click Administrative Templates, and then click Printers.
- Right-click Point and Print Restrictions, and then click Edit.
- In the Point and Print Restrictions dialog, click Enabled.
- Select the Users can only point and print to these servers checkbox if it is not already selected.
- Enter the fully qualified server names. Separate each name by using a semicolon (;).
- In the When installing drivers for a new connection box, select Show warning and Elevated Prompt.
- In the When updating drivers for an existing connection box, select Show warning and Elevated Prompt.
- Click OK.
Permit users to only connect to specific Package Point and Print servers that you trust
This policy, Package Point and Print - Approved servers, will restrict the client behavior to only allow Point and Print connections to defined servers that use package-aware drivers.
Use the following steps:
- On the domain controller, select Start, select Administrative Tools, and then select Group Policy Management. Alternatively, select Start, select Run, type GPMC.MSC, and then press Enter.
- Expand the forest and then expand the domains.
- Under your domain, select the OU where you want to create this policy.
- Right-click the OU and then select Create a GPO in this domain, and link it here.
- Give the GPO a name, and then select OK.
- Right-click the newly created Group Policy Object and then select Edit to open the Group Policy Management Editor.
In the Group Policy Management Editor, expand the following folders:
- Computer Configuration
- Policies
- Administrative Templates
- Local Computer Polices
- Printers
- Enable Package Point and Print - Approved servers and select the Show... button.
- Enter the fully qualified server names. Separate each name by using a semicolon (;).
The next step is to add the following registry key to your group policy that applies to your computers. Make sure it is set the DWORD to 0.
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows NT\Printers\PointAndPrint" RestrictDriverInstallationToAdministrators /REG_DWORD 0
What happens if you don't implement these steps and you have point and print enabled?
After patches/reboots and just random times, your users will get prompted to reinstall drivers. Even if the drivers are installed locally, they will still be prompted. I opened a call with Microsoft as that was not suppose to be the behavior, but it is. At first it was reported as a bug, but then they said they are not going to fix it.
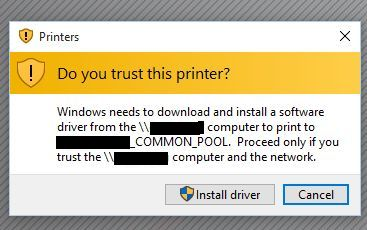
Microsoft also released another patch to address print nightmare in September, which is causing prompts again. Microsofts advice, found here is to make sure your print drivers on your print server and clients are the same. You also need to make sure you are patched to at least January of 2021, if not your users will unable to print.
While this does still leave you slightly vulnerable, the vulnerability is very low. If someone would happen to attack your print servers and place malware on them, you have a much bigger problem on your hand.
I should have published this article a month ago when I addressed this issue, but I am bit behind in my blog posts. If you are still experiencing this issue, I hope this helps.
