I have been working on a project to move away from VMWARE Airwatch and migrate over to Microsoft Intune. One of the items on the to-do list was to mirror the functionality of the AirWatch Tunnel, allowing mobile devices to create an on-demand VPN tunnel when then need access to corporate resources.
Microsoft has two ways to accomplish this, leverage Microsoft Tunnel for Intune or leverage a VPN tunnel from one of the many VPN/Firewall manufactures. Since Palo Alto is our firewall of choice, we chose to leverage Palo Alto.
Microsoft makes it relatively easy to configure this option for IOS, but the Android configuration is devoid of articles on how to get it configured. I thought I would provide a guide on how to configure this and same some the trial and errors I went through to get this running.
Configuration Details
Since these are mobile devices and I did not want to have users enter passwords each and every time they needed to bring up a tunnel, we leveraged PKCS to deploy certs to mobile devices. The other option is SCEP, I am not going to get into the pro's and con's of each, but will link an article here that gets into that topic. In my opinion, I would go with PKCS unless you have a team that can devote time to maintain and manage SCEP.
I also wanted to leverage Palo Alto's HIP check to limit access to only the systems the mobile devices needed access to.
PFX/PKCS, Active Directory Certificate Services and Intune.
I am not going to get into that configuration in this article, but listed below are a few good resources on how to configure and troubleshoot that configuration.
Configuraiton and Troubleshooting
Another Good Article On Configuration
Good Article on Troubleshooting PKCS Cert Deployment
Palo Alto Firewall's
The information below is the actions you will need to perform on your Palo Alto firewall to allow mobile devices to connect leveraging the certificate obtained from your internal Certificate Authority (CA) Server.
Exporting Certs
So there are multiple methods to export your trusted root one way is from your ADCS running from a command prompt elevated.
certutil -ca.cert <path and file name ending in .cer>

Another is directly from any domain joined workstation.
Running MMC.exe as admin, you can export y our current Trusted Root and Intermediate. Depending on your CA architecture you may need both especially if your root is offline and your using an issuing CA.

Certificates
Once you have export the certificates from the above step, you will Place them in Device --> Certificate Management --> Certificates.
You will need to create a certificate profile that the firewall will leverage to authenticate the mobile users, this certificate needs to have a certificate profile that includes your public certificates from your root certificate authority server and if you have a subordinate certificate authority server.
The profile will look like the screen below. It will be located in Device --> Certificate Management --> Certificate Profile.
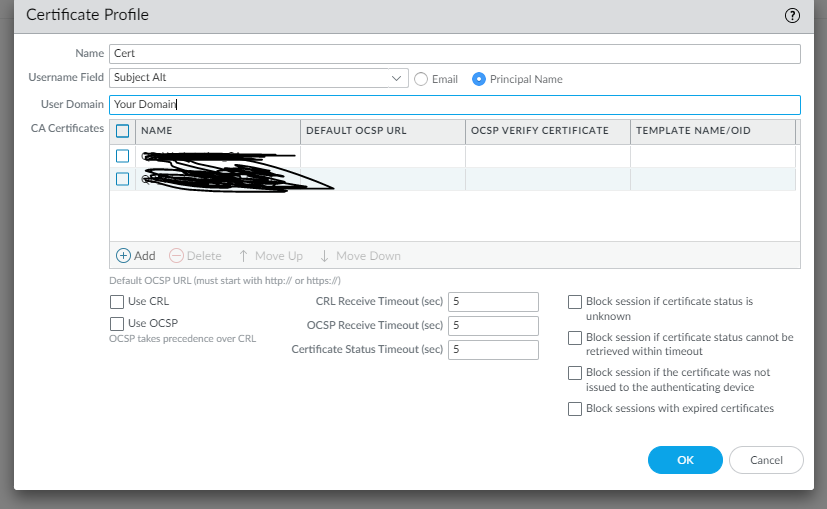
VPN Tunnel Configuration
The next step is to create a VPN Tunnel, to do that, go to Network --> Global Protect --> Portals
You will create a portal the is used exclusively for Intune/Mobile devices. You can assign motilities IP Addresses to a Palo Alto firewall, so if you have an existing VPN tunnel on your Palo Firewall, just assign another IP address.
Name the Portal (I will like to name it the same as the DNS name used to access the VPN tunnel).
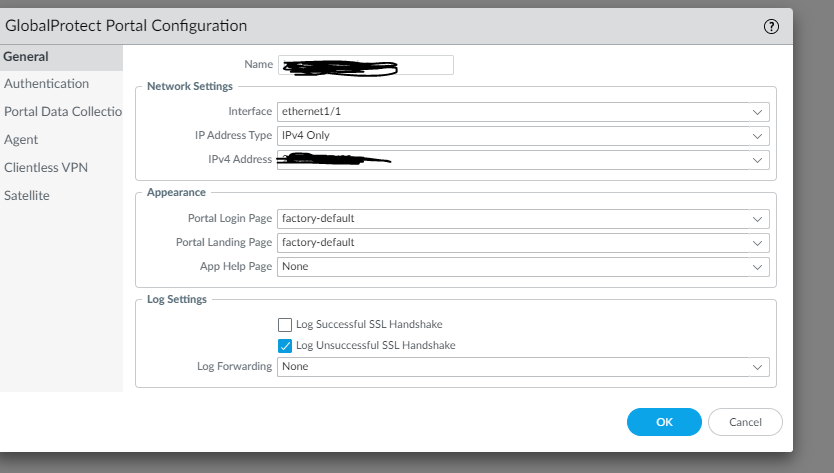
You will need to have a certificate installed on your firewall with the name that will be used by your clients to connect to the VPN. This should be signed by a public CA. I am not going to list those steps here, those are easy to find on the Palo Alto knowledge base and website.
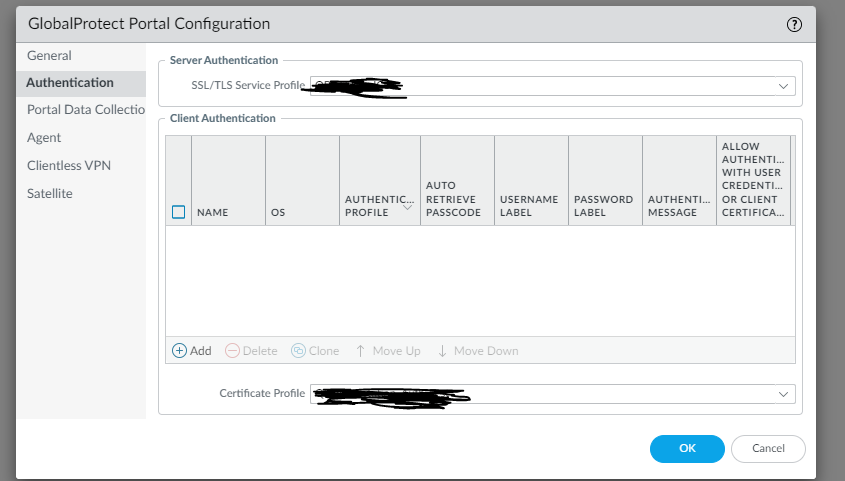
You will need to set the authentication to leverage the certificate profile you created in the step above.
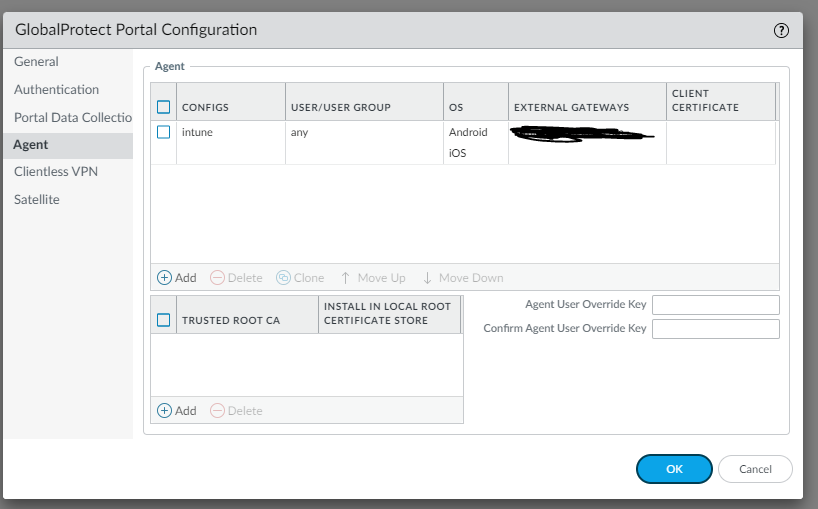
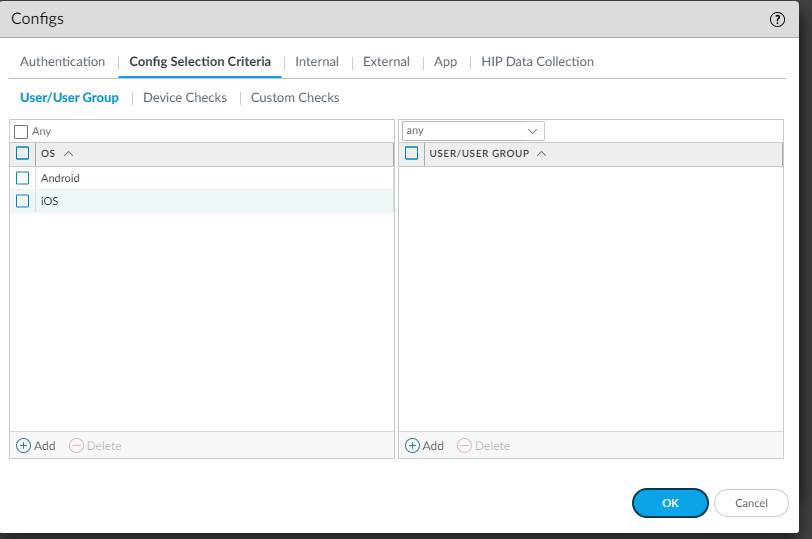
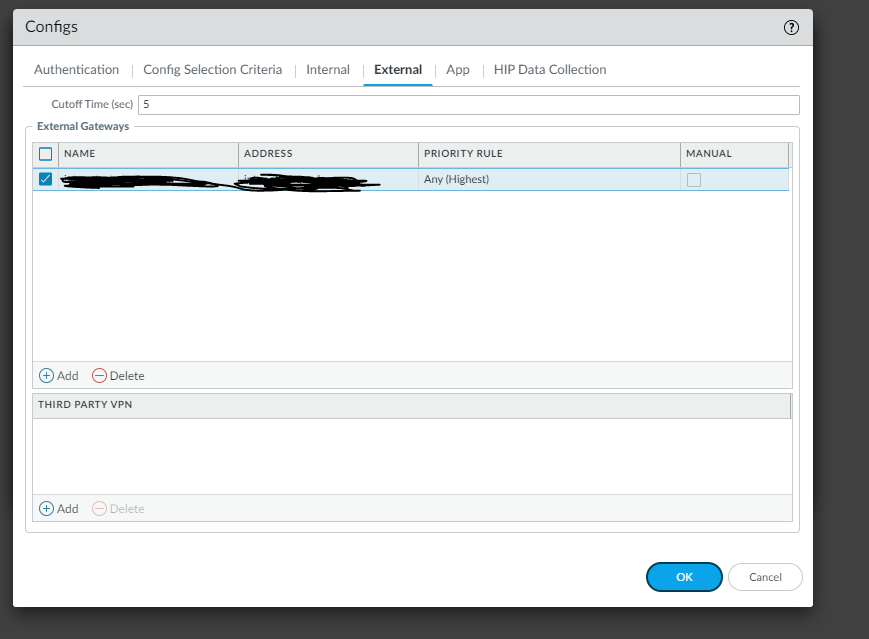
In the agent configuration, you will want to make sure you provide the name of the gateway you would like the mobile devices to connect to. You also want to limit the OS to Android and IOS, this allows you to identify the mobile devices and limit them in the firewall rule base.
This what the configuration in the authentication screen should look like. If you want to allow cookies to reestablish a VPN tunnel, then select the public CA certificate you purchased and leverage that to encrypt/decrypt cookies.
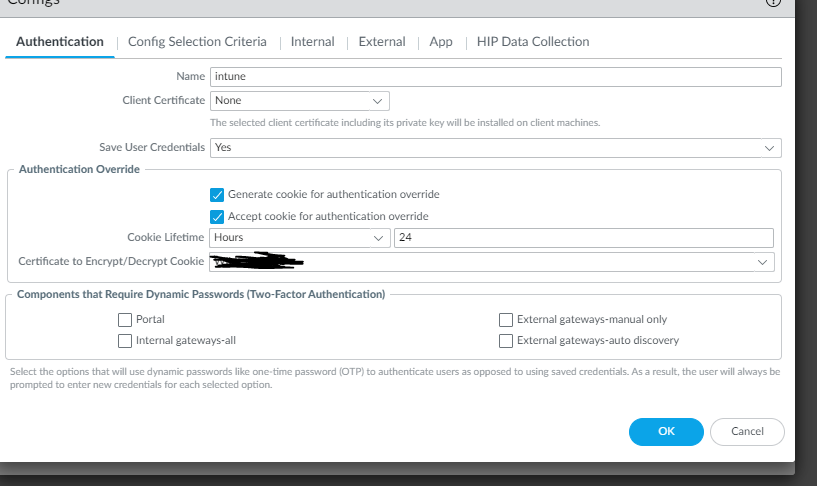
This is the location you can limit the operating system (OS) type that connects.
Define the name and address of the gateway the mobile clients will be connecting to.
Set the connect method to be on-demand.
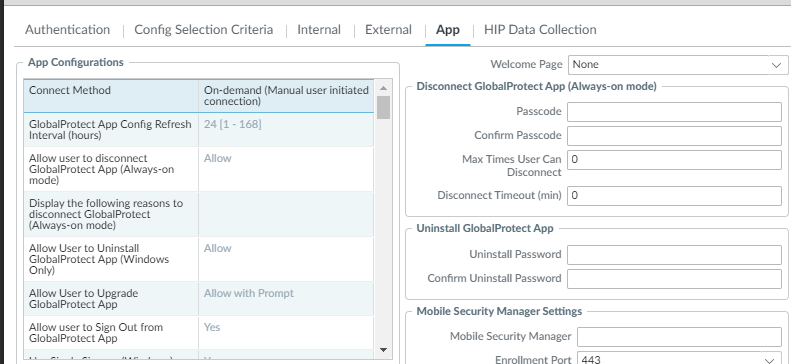
Select the checkbox to Collect HIP data, this will allow for the ability to collect OS type.
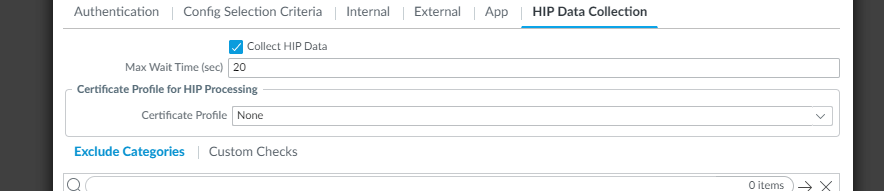
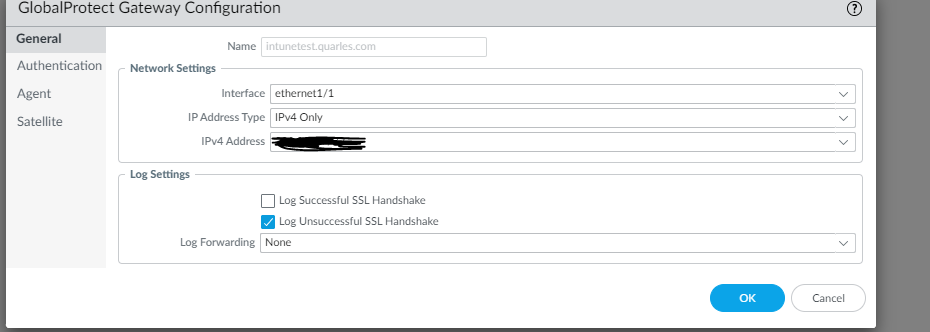
The next step is to create a gateway. Go to Network --> GlobalProtect --> Gateways
Select the Interface that the VPN tunnel will be terminated and the IP address is should be listening on.
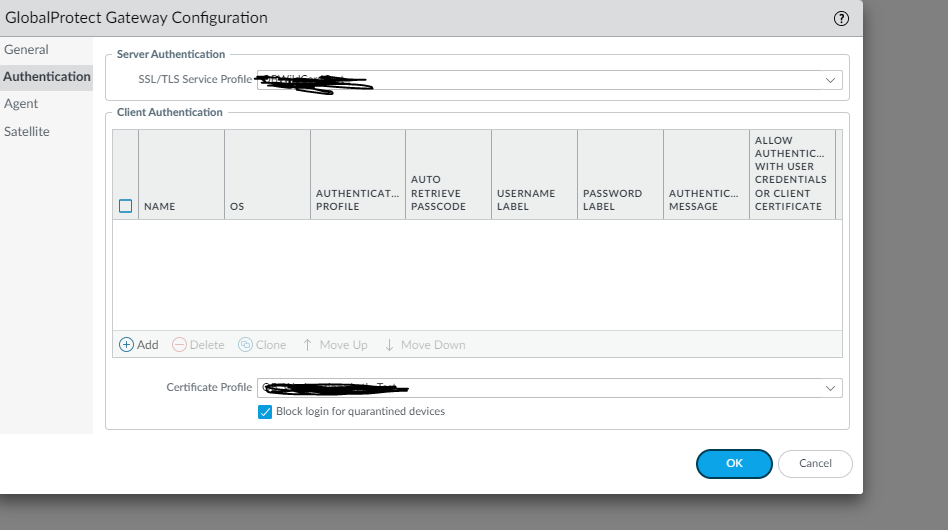
Select the server authentication profile and the certificate profile you created.
For Agent, you will configure the following. Give the tunnel a unique interface and enable IPSEC.
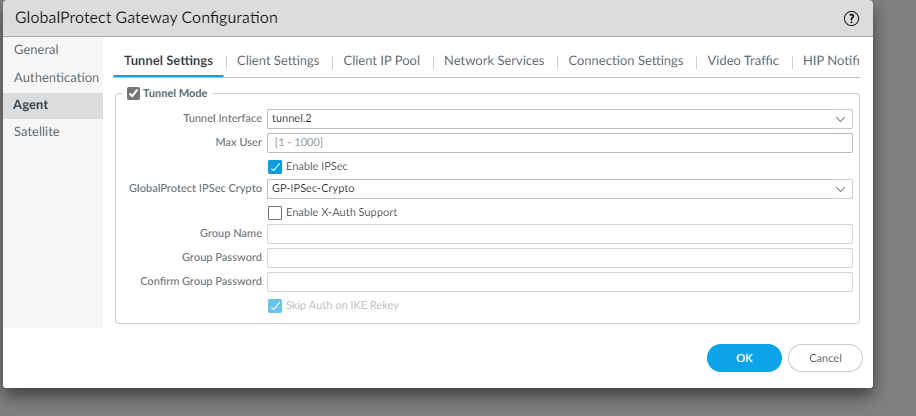
Select the network that the VPN tunnel will allow access to.
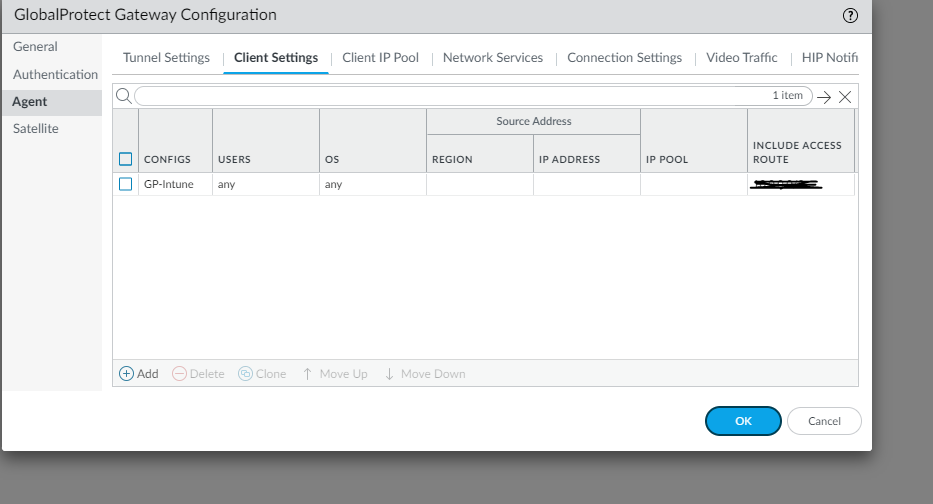
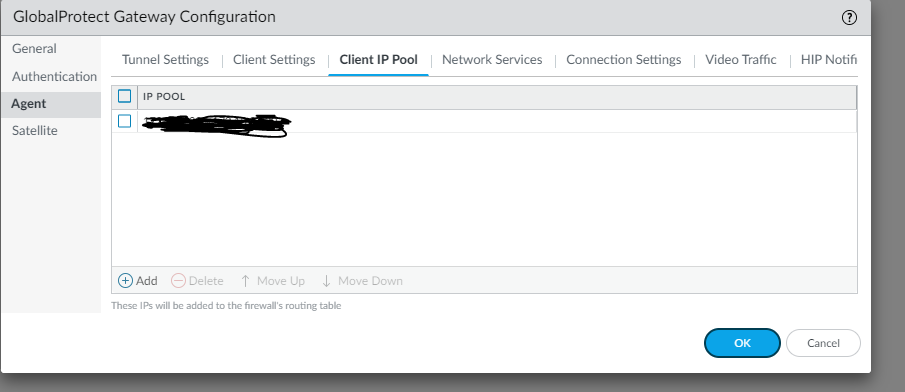
Configure the Client IP Pool. This will be the IP address pool you will be handing out to the mobile clients.
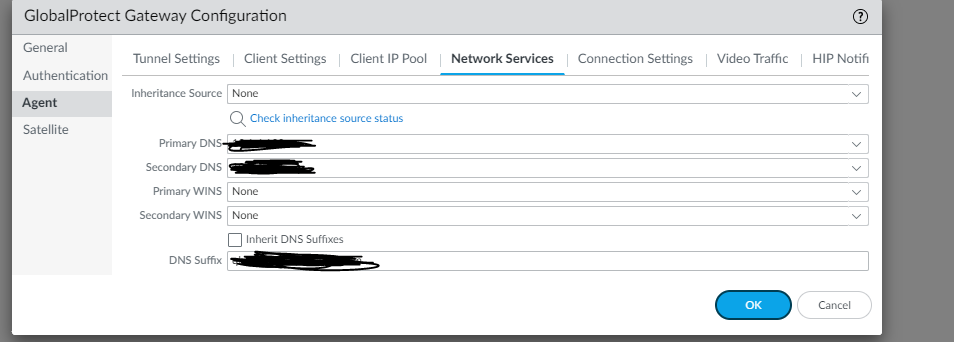
You will need to setup the Primary and Secondary DNS and the DNS suffix you want to assign to the tunnel.
Firewall Ruleset
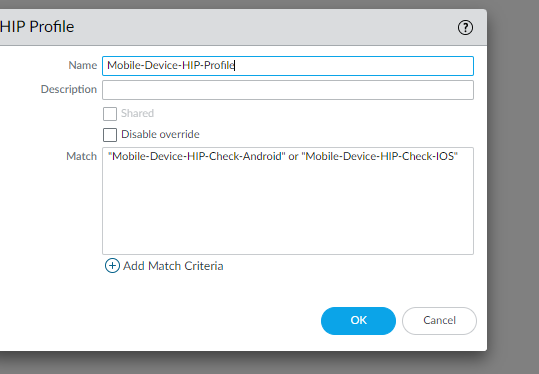
You will need to create a HIP profile to identify the mobile devices. This will be used in the firewall rule that you create. To create a HIP profile, go to Objects --> Global Protect --> HIP Profiles. The profile will look like the profile below.
One that has been completed, you will need to create a firewall rule to allow access to the resources on your network. I am not going to show every screen shot on how to c0nfigure this, but you will want to limit it to the users who should be connecting, the hosts/servers you want the mobile devices to connect to and limit it to the services you want to allow.
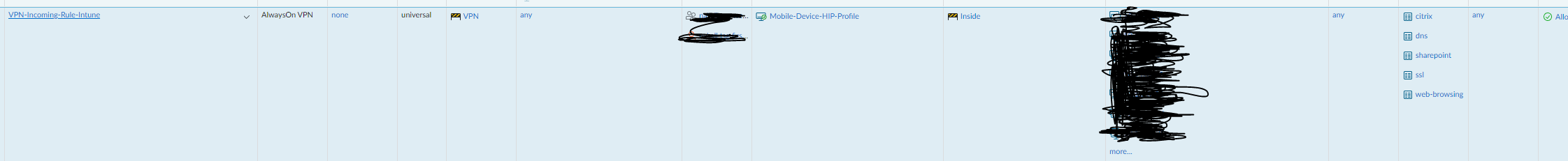
Intune Configuration
Now that you have the firewall configured, it is time to configure Intune. I wish Microsoft had better support for Android's with VPN tunnels.
Android Certificate Profile
The first step is to create a device configuration profile for Android to push out the CA public certificates to your mobile devices and to setup the SCEP request.
You will need to be logged into https://endpoint.microsoft.com/ with an account that has the proper rights to create profiles for devices.
Go to Home --> Devices | Android--> Configuration Profiles.
Create a Profile for Your Root CA Cert bundle.
Select create profile, select Android Enterprise and profile type of Trusted Certificate
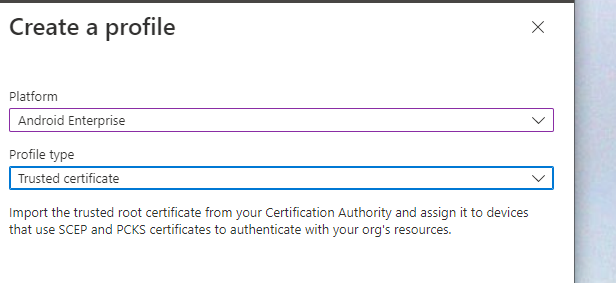
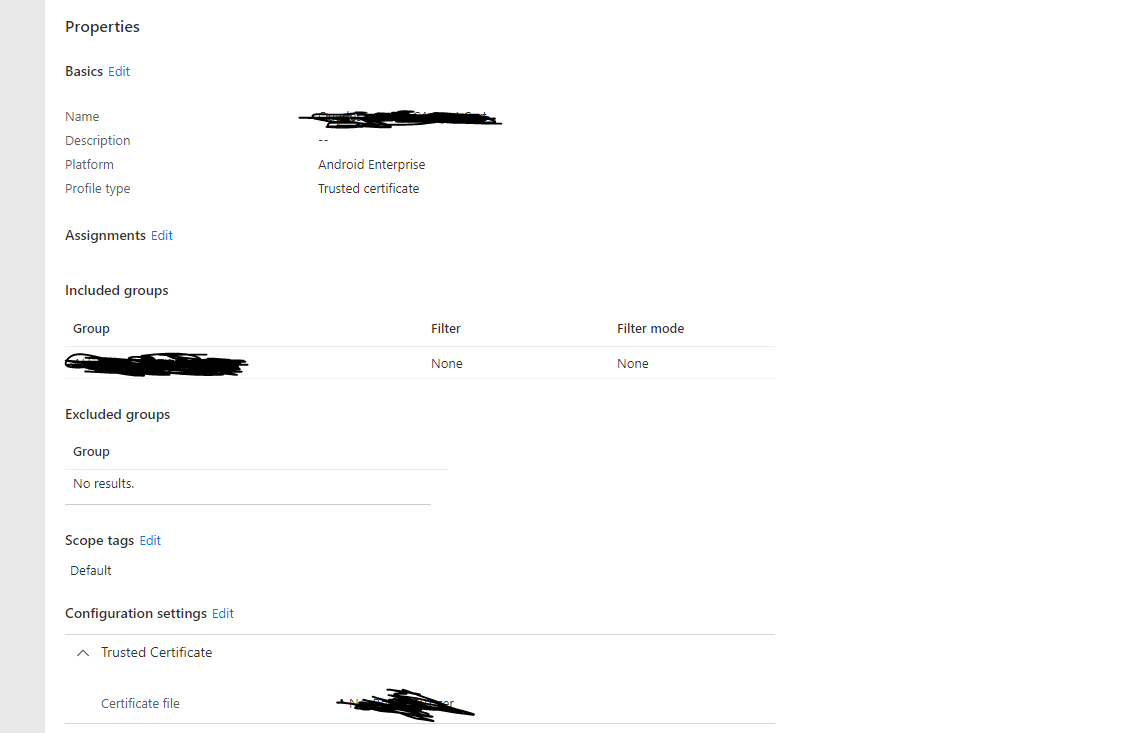
You will need to provide a name, a group to deploy the certificate to and finally the root ca bundle file.
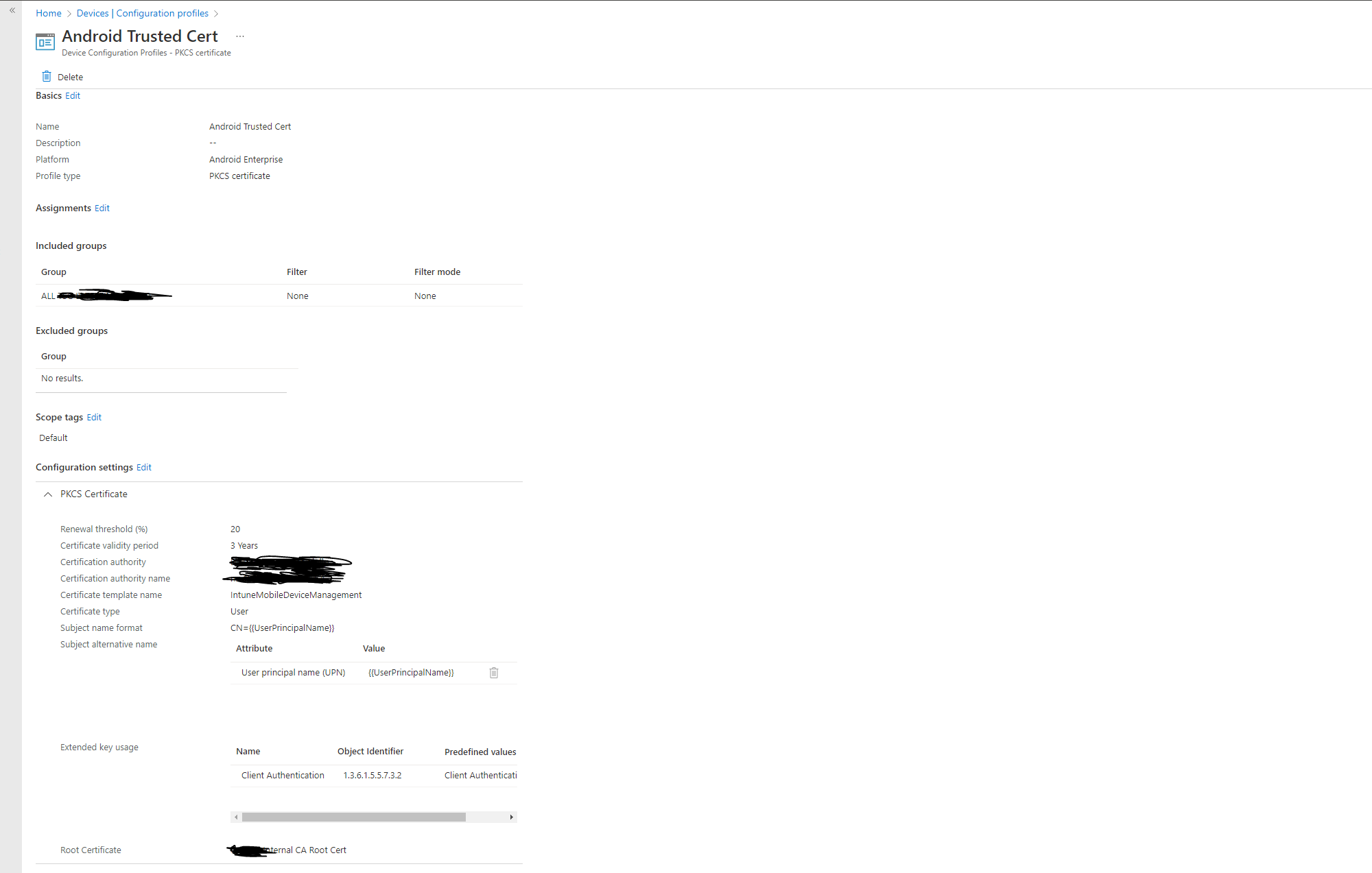
Create a profile for a PKCS Certificate.
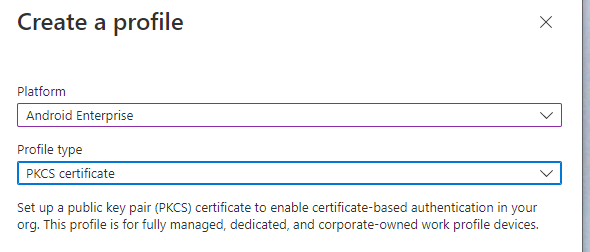
You will need to give it a name and a group to deploy this to. You will also need to select the name of the certificate authority (Which should be the DNS name of your certificate authority server handing out certs) and certificate authority name (The Name you called your Active Directory CA Server, which is generally separate from the DNS name). The cert type should be user and the need to have the subject name format as CN={{UserPrincipalName}}. You also need to set the subject alternative name to look like this, AttributeValueUser principal name (UPN){{UserPrincipalName}}. The VPN tunnel will fail without the subject alterative name. A good way to find the name is to run the following certutil command, certutil -config - -ping
The certificate Template Name is the Template Name your have created on your Active Directory certificate server. This is the template the mobile device will use when requesting a certificate.
Finally, make sure you have this listed as the Extended Key Usage Client Authentication1.3.6.1.5.5.7.3.2Client Authentication.
Finally, you will need to select the CA bundle you created in the prior step.
Global Protect App For Android
I am not going to list the steps here, but you will want to make the Global Protect for Android application available before creating the application profile below.
Global Protect Application Profile
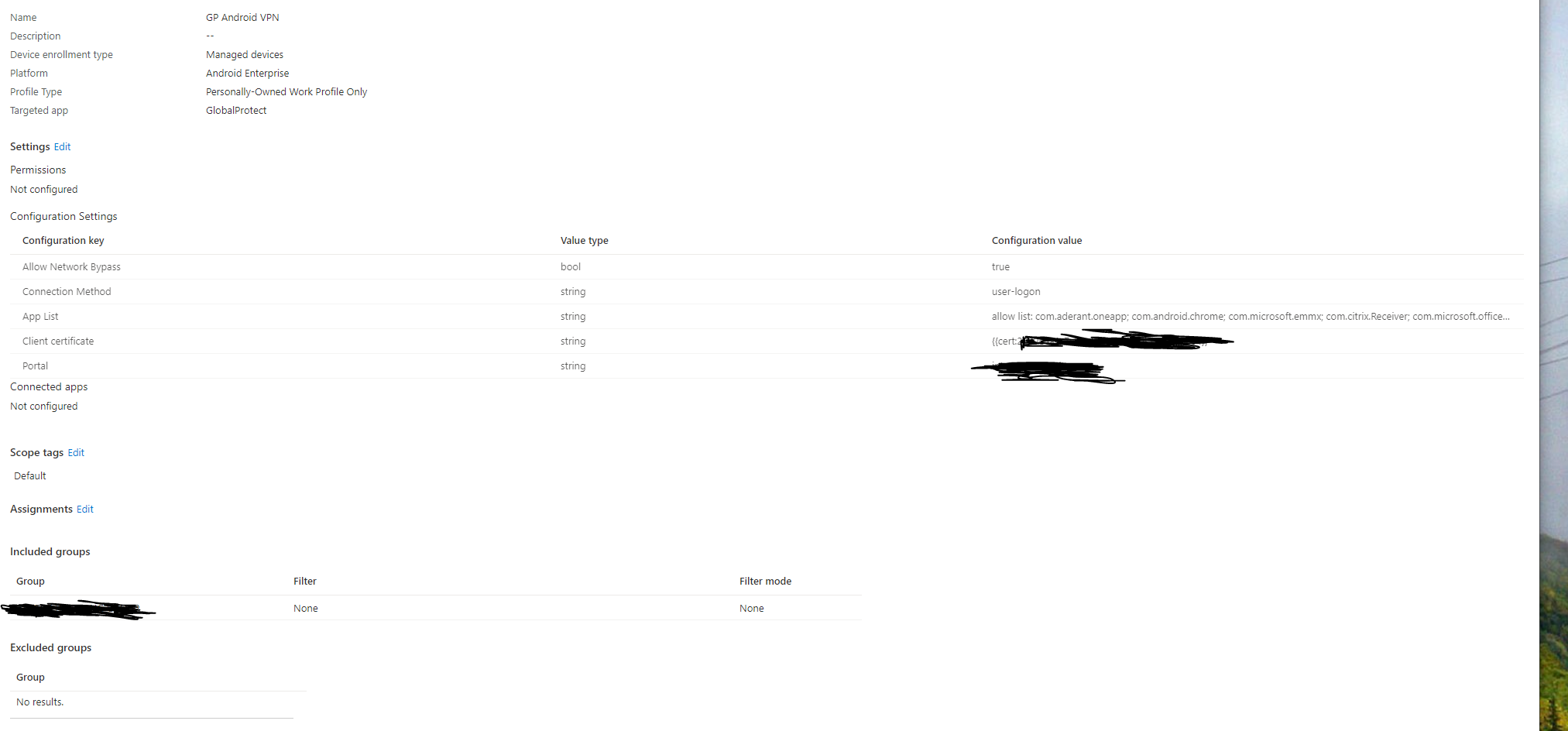
Then go to Home --> Apps --> App Configuration Profile.
You will want to create an application configuration profile for Global Protect.
The settings will look like the setting below. If you do not want to tunnel all traffic to the VPN, set the Allow Network Bypass to true, the network login type should be user-login, the App-List is the applications you want to allow to use the tunnel. This article describes how to obtain that name. Finally the client certificate is important.
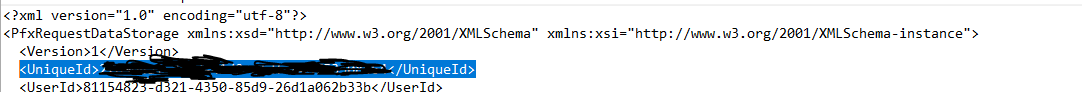
The method I used obtained the client certificate ID was to look at the request in the logs on the server you have the Intune Cert Connector for Microsoft Intune Installed . If you go to the logs in the following director, C:\Program Files\Microsoft Intune\PFXCertificateConnector\PfxRequest\Succeed and look at a successful request, you will see an entry in the log file that looks like this, the value in the unique ID is what you want to place in the client certificate. I am sure a better way exists to find this ID, but I have yet to find it. If someone knows a better way, let me know, email me at james@oryszczyn.com.
Final Thoughts
I hope this helps configure the Global Protect Client for Android using an Intune application profile. I hope Microsoft builds this configuration into a wizard, much like they have for IOS. This configuration took me quite some time to put together and troubleshoot, so I hope this saves you a bunch of time.
